
Home
Services
About us
Blog
Contacts
Drone Detection Apps in 2025: Custom Mobile Solutions by A-Bots.com
1. The New Threat Landscape: Why Drone Detection Matters Now
-
Proliferation of consumer & prosumer UAVs, recent high-profile incursions
-
Regulatory push: FAA Remote ID, EU U-Space, Kazakhstan’s civil-aviation rules
-
Detection technology matrix (6 methods):
- RF spectrum analyzers / signature libraries – real-time intercept of C2 links
- Passive radar / multilateration – exploiting reflected commercial broadcast signals
- ADS-B & Mode-S sniffing – decoding cooperative transponders on larger UAVs
- Acoustic arrays – microphone clusters & ML classifiers for rotor noise patterns
- EO/IR optical-AI fusion – day/night computer-vision tracking with object detection models
- Thermal & multispectral imaging – long-wave IR to spot low-visibility or dark-painted drones
-
Key deployment scenarios: critical infrastructure, stadiums, events, border zones, corporate campuses
2. From Sensors to Screen: Architecting a Drone Detection Mobile App
- Data-fusion pipeline: edge classification → encrypted stream → cloud analytics
- Mobile UX patterns for situational awareness (heat-maps, 3-D flight paths, AR overlays)
- Real-time alerts & escalation workflows (SMS, push, API hooks for PSIM/VMS)
- Performance & security considerations: low-latency WebSockets, zero-trust auth, offline-first modes
- Integration with existing hardware vendors (DJI AeroScope, Dedrone RF-360, custom SDR rigs)
3. Custom Implementation Roadmap with A-Bots.com
- Discovery workshops & threat-modeling sprints
- MVP in 90 days: sensor SDK integration, core alert engine, pilot deployment
- Scaling to enterprise: multi-site orchestration, SaaS dashboards, white-labeling for integrators
- Compliance & future-proofing: data-residency, AI model updates, continuous DevSecOps
- Why A-Bots.com: track-record in drone software, ISO-certified processes, flexible engagement models
1. The New Threat Landscape: Why Drone Detection Matters Now
By mid-2025 the global conversation around drones has shifted from “How can we use them?” to “How can we coexist with them safely?” Consumer and prosumer quadcopters that once symbolised harmless weekend hobbies now generate daily operational, legal, and reputational headaches for airports, stadiums, utilities, border forces, and corporate campuses alike. Three converging forces explain why every security blueprint drafted this year contains a line item for mobile-first drone-detection applications.
1.1 An escalation of real-world incidents
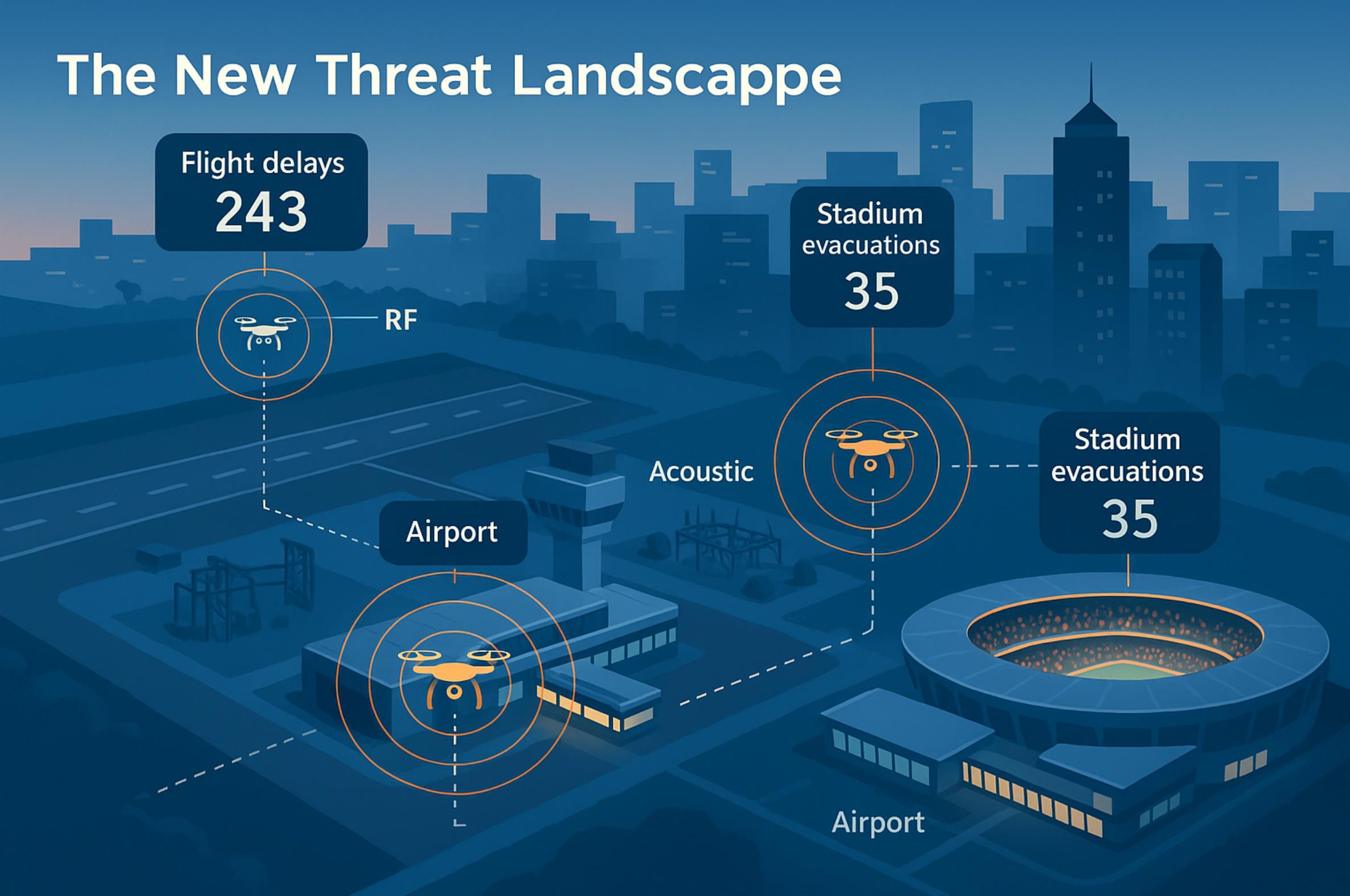
- Air-transport disruption. In the past eighteen months dozens of large commercial airports—from London Gatwick to Singapore Changi—have imposed partial closures or runway holds after unverified drone sightings. Even a ten-minute ground stop can cascade into hundreds of delayed flights, contractual penalties for carriers, and overtime bills for ground crews.
- Critical infrastructure under pressure. Power-grid operators, petrochemical complexes, and data-centre providers now track hundreds of unauthorised over-flights per quarter. The mere suspicion that a drone is surveying a substation or flaring stack is enough to trigger lockdown protocols, divert maintenance teams, and prompt incident reporting to regulators.
- Sporting and entertainment venues. Stadium managers in North America and Europe report that drone incursions on match days have grown from occasional curiosities in 2019 to a near-weekly occurrence in 2024 – 2025. Suspended play, broadcast delays, and the need to evacuate seating areas translate directly into lost ticket revenue and insurance claims.
- Correctional facilities and borders. Small multirotors are now the contraband delivery system of choice for organised crime. For every high-profile interception reported in the press, dozens of successful drops never make the headlines, further incentivising illicit operators to scale their fleets.
- Corporate espionage and privacy breaches. High-end camera drones hovering over research campuses or executive residences can capture product prototypes, licence-plate data, or sensitive conversations from vantage points unreachable by traditional CCTV.
Each headline represents real money: diverted flights, halted production lines, match-day refunds, forensic investigations, and reputational harm. For boards of directors and city councils the question is no longer if but how fast to deploy counter-UAS technology—and how to surface its insights on the devices security teams already carry.
1.2 Tightening regulatory screws
Legislators on three continents have made detection not merely a best practice but a compliance prerequisite.
- United States. The FAA’s Remote ID rule became fully enforceable in March 2024. All drones weighing more than 250 g (save for a handful of exceptions) must broadcast identity, location, and take-off point. Non-compliant pilots risk civil fines and certificate revocation.
- European Union. The U-Space framework, which mandates network-based identification and air-traffic coordination for unmanned aircraft, is now rolling out corridor by corridor across member states. Operators entering an activated U-Space cell must share flight plans and respond to de-confliction commands in real time.
- Kazakhstan and Central Asia. New civil-aviation rules cap recreational drones at 1.5 kg, impose 100- to 150-metre standoff distances from buildings, and require commercial users to secure permits. While penalties vary by oblast, local police increasingly ask venue owners to prove they can detect and log violators.
- Event-specific bans. Temporary Flight Restrictions—so-called No-Drone Zones—now accompany major sports finals, heads-of-state visits, and open-air concerts. Organisers must show they can detect and geolocate rogue aircraft within seconds or risk losing their licence.
Compliance cuts both ways: it obliges authorised pilots to broadcast telemetry, but it also empowers defenders to scan the spectrum, correlate IDs, and act before a quadcopter crosses a sensitive perimeter.
1.3 Six complementary detection methods—there is no single silver bullet
Seasoned counter-UAS programmes layer multiple sensing modalities to maximise probability of detection and minimise false alarms. Below is the 2025 state of the art, presented as a narrative matrix rather than a table:
- RF Spectrum Analysis & Signature Libraries. Wide-band software-defined radios (SDRs) capture command-and-control emissions in the 2.4 GHz, 5.8 GHz, and sometimes LTE bands. Machine-learning classifiers fingerprint vendors and even specific firmware versions, while time-difference-of-arrival algorithms triangulate pilot location. Strengths: near-instantaneous detection of active links, ability to attribute control stations. Limitations: blind to pre-programmed, radio-silent sorties; success hinges on keeping signature libraries current. Pairing with radar or optics closes most gaps.
- Passive Radar & Multilateration. Instead of emitting their own pulses, passive systems exploit existing illuminators—digital-TV towers, FM broadcast, 4G/5G base stations—and track Doppler shifts or signal-arrival discrepancies. Strengths: completely covert (the adversary cannot detect your sensors), immune to jamming, effective against low-reflectivity plastic airframes. Limitations: performance depends on local broadcast density and complex signal processing; high false-positive rates in cluttered urban canyons unless reinforced by thermal imagery.
- ADS-B & Mode-S Interrogation. Heavier UAVs and all eVTOL air-taxis are required to carry transponders that echo unique 24-bit addresses, altitude, and velocity. Portable receivers can plug straight into detection stacks or even consumer mobile devices. Strengths: positive identification tied to civil-aviation databases; straightforward compliance auditing. Limitations: irrelevant for hobby-class multirotors under 250 g; spoofed or disabled transponders remain a threat vector.
- Acoustic Arrays. Distributed microphone clusters capture rotor-noise signatures; convolutional neural networks classify patterns against an ever-growing corpus of recordings. Strengths: superb coverage behind obstacles and foliage, low power requirements for remote borders or prison perimeters. Limitations: highly weather-dependent; heavy rain or urban jackhammers can drown out cues. Adaptive filtering and cross-referencing with RF data mitigate false alarms.
- EO/IR Optical-AI Fusion. Daylight electro-optical cameras and night-time infrared sensors stream frames to edge GPUs running modern detection networks such as YOLOv8 or DETR derivatives. Strengths: delivers the “smoking-gun” visual confirmation that regulators and juries expect; enables long-range tracking with pan-tilt-zoom mounts. Limitations: glare, cloud cover, and the simple fact that a 40-cm drone can disappear against complex backgrounds; tasking logic should cue cameras only when RF or radar suggests a target.
- Thermal & Multispectral Imaging. Long-wave-IR cameras detect the motor-heat signature of battery-powered drones, while multispectral payloads highlight the distinct reflectance of plastic and metal composites. Strengths: invaluable for night operations and border patrol, capable of spotting dark-painted or light-masked craft. Limitations: pricey hardware and prodigious bandwidth demands; smart region-of-interest cropping and cloud off-loading preserve network budgets.
Field experience shows that most high-risk deployments rely on at least two of these channels running in concert—for example RF plus EO/IR for stadiums, or acoustic plus passive radar for correctional facilities. The fusion itself is where much of the intellectual property lives: correlating detections within a 200-millisecond window, weighting sensor confidence, and triggering graduated responses from silent logging to active disruption.
1.4 Why mobile-first delivery matters
The era in which counter-UAS data lived exclusively on wall-mounted consoles has ended. Today every responder carries a ruggedised smartphone or tablet that already feeds incident-management workflows, building-automation systems, and body-cam streams. A properly engineered drone-detection app turns those devices into tactical air-defence terminals:
- Ultra-low-latency awareness. WebSocket or MQTT streams push detections from edge appliances to handheld screens in under 300 milliseconds. Animated heatmaps and three-dimensional flight paths render via the device GPU, while Augmented Reality overlays let the user point the camera skyward and see an intruder’s vector in context.
- Context-driven decision support. The app can query NOTAM feeds, check whether a Remote ID matches an authorised survey mission, and autofill escalation workflows. Push notifications route to the nearest security officer, while REST hooks pass metadata to PSIM and VMS platforms without human intervention.
- Evidence lifecycle in your pocket. Encrypted logs, SHA-256 hashes, and time-synchronised video clips sync to cloud storage compliant with ISO 27001, FedRAMP, or the European Cybersecurity Act. Generating a prosecutorial bundle becomes a one-tap export rather than a week of paperwork.
Organisations piloting such applications report 30 – 50 percent faster threat resolution compared with legacy radio call-trees and desktop dashboards, all while lowering total cost of ownership by re-using fleet devices instead of buying proprietary handsets.
1.5 From reactive measure to strategic differentiator
Counter-UAS is no longer an exotic line item reserved for defence primes; it has become an operational necessity akin to firewalls and CCTV. Yet many enterprises remain paralysed by the complexity of integrating heterogeneous sensors, cloud analytics, and intuitive mobile UX into one cohesive system.
This is precisely where A-Bots.com—with its decade-long track record in drone telemetry, drone mapping software, computer-vision pipelines, and cross-platform app frameworks—creates tangible value. By abstracting sensor diversity behind well-maintained SDKs, implementing zero-trust authentication out of the box, and optimising data flows for sub-second delivery, an A-Bots-powered solution converts raw sensor feeds into actionable intelligence for everyone, from the stadium command post to the lone utilities technician patrolling a remote substation.
In a threat landscape that evolves faster than air-law handbooks can be updated, the true competitive edge lies in how quickly an organisation can iterate on its detection UI, roll out new RF signatures, and plug into existing security ecosystems. Sections 2 and 3 will map exactly how to achieve a 90-day MVP and why leveraging the A-Bots.com tool-chain makes that aggressive timeline realistic.
2. From Sensors to Screen: Architecting a Drone Detection Mobile App
Building a counter-UAS platform that actually helps frontline personnel starts long before the first line of mobile code is written. It begins at the sensor edge, travels through compressed data pipelines and scalable cloud analytics, and ends in a palm-sized UX that must convey life-critical context in milliseconds. The following blueprint shows how the most effective 2025-era systems move information from spinning rotors in the sky to actionable pixels on a smartphone.
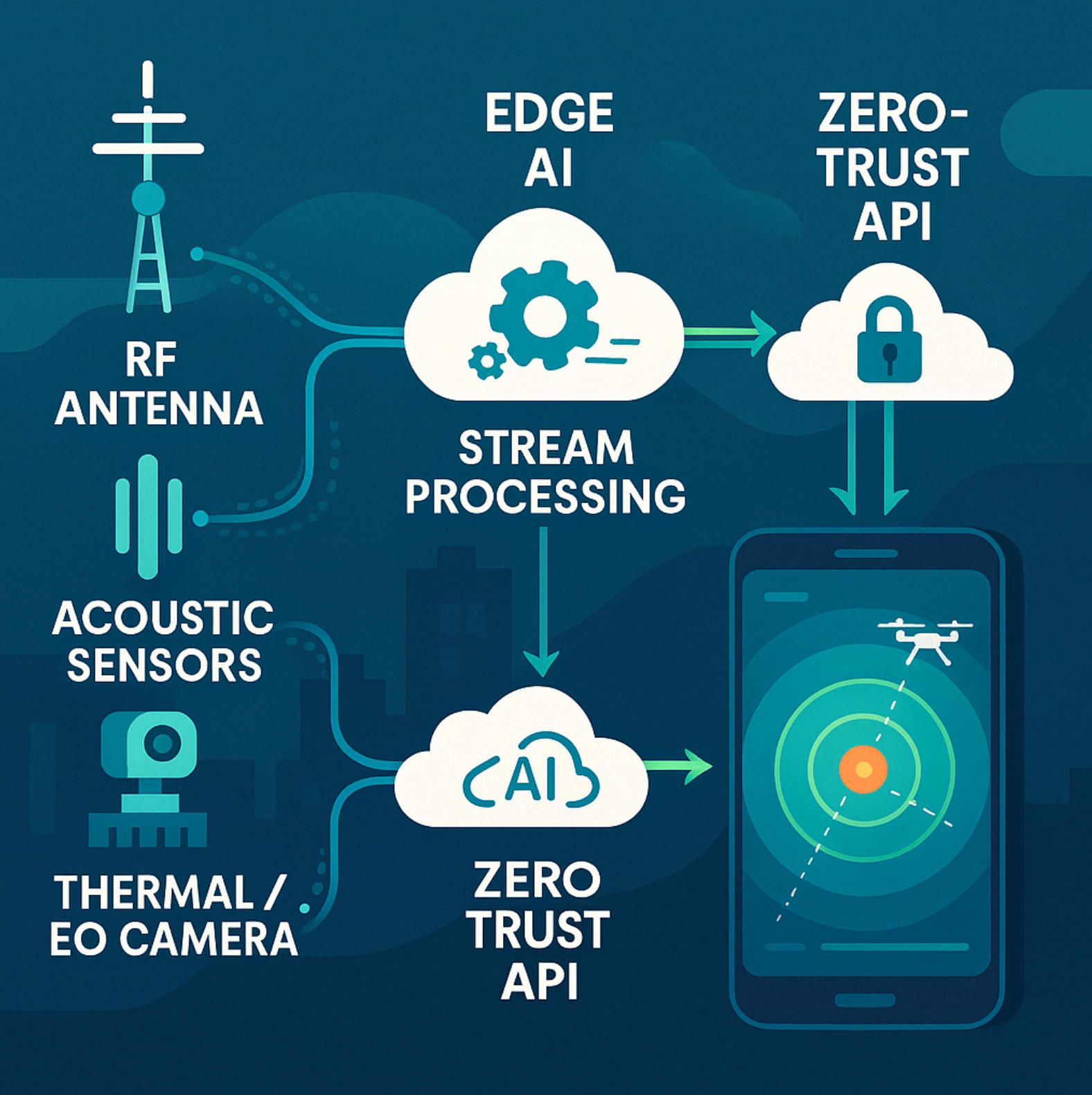
2.1 Data-fusion at the edge: normalise first, analyse fast
A typical deployment involves a heterogeneous stack: passive RF receivers, acoustic microphones on prison walls, EO/IR gimbals atop stadium roofs, and perhaps a pair of low-power thermal imagers along a fence line. Each device ships logs in its own dialect, timestamp precision, and coordinate frame. The first architectural mandate is therefore normalisation close to the metal. Containerised micro-services running on an ARM-based gateway translate raw packets into a unified protobuf schema; GPS-disciplined oscillators and IEEE 1588 PTP keep clocks within sub-millisecond skew so that fusion logic downstream can apply sliding windows without painful heuristics.
Critically, edge nodes perform lightweight inference—for example, a YOLOv8-Tiny model prunes 90% of empty optical frames, while an on-device CNN discards acoustic segments that score below 0.25 drone-likelihood. This step slashes backhaul bandwidth and shaves latency budgets from seconds to hundreds of milliseconds, enabling real-time alerts on consumer LTE uplinks.
2.2 Message buses that survive burst traffic
The gateway forwards enriched events to a backbone built on NATS JetStream or Redpanda-compatible Kafka topics. Both deliver at-least-once guarantees and horizontal scalability, but their choice hinges on operational nuance: JetStream shines in geographically dispersed clusters with intermittent links, whereas Kafka excels in dense campus architectures where terabytes of optical imagery flood the wire every hour.
Inside the stream, a Flink or Apache Pulsar compute layer performs geospatial joins—merging an RF hit at bearing 195° with a passive-radar track 300m north of the fence, then emitting a fused “tentative target” object. Sliding-window analytics assign confidence scores, while stateful operators de-duplicate chatter when a single quadcopter triggers five sensors simultaneously.
2.3 Cloud analytics and continuously trained AI models
Events that survive edge and stream pruning land in a cloud-native analytics tier—often built on Kubernetes, ArgoCD, and serverless GPU pools. Here, heavier computer-vision models (DETR-3D, Mask2Former) refine bounding boxes, and an unsupervised anomaly detector flags signatures that match neither library fingerprints nor known transit routes. Model-as-data practices—DVC for versioning, MLflow for experiment tracking, Argo Workflows for scheduled retraining—ensure that new C2 protocols or rotor noise profiles propagate from data lake to production without human heroics.
To maintain sub-second end-to-end latency, inference results enter a Redis-backed low-latency API layer that caches hot entities (“DJI Mavic 3 detected, 82% confidence”) for 15–30 seconds—long enough for frontline devices to poll once and still act on fresh data.
2.4 API gateway and zero-trust security
Mobile apps speak to the platform via a gRPC façade wrapped in Envoy sidecars. mTLS with short-lived service certificates blocks rogue listeners, while OAuth 2.1 and OpenID Connect scopes map cleanly onto operational roles: guard, supervisor, or third-party law-enforcement liaison. Every request flows through policy-as-code gates (OPA / Kyverno), guaranteeing that a subcontractor can subscribe to alert streams but never download historical video from the wrong site.
Rate limiting is intentional: on a stadium network with 150 guards connected, a drone swarm could trigger thousands of pushes per minute. An adaptive leaky-bucket algorithm collapses burst traffic, sending the first alert at full fidelity, subsequent updates as incremental deltas, and a final summary when the incident closes.
2.5 Designing situational-awareness UX that operators trust
A drone-detection screen competes with radios, CCTV monitors, and the chaotic acoustics of a live venue. Effective mobile UX therefore follows three core patterns:
- Glanceable heat-maps that encode risk by colour and opacity, allowing a guard to know at five metres which sector is hot even with peripheral vision.
- Three-dimensional flight trajectories rendered in WebGL; pinch-to-zoom climbs altitude layers, while a two-finger scrub rewinds object history to cross-reference with CCTV timestamps.
- Augmented-Reality overlays powered by ARCore/ARKit: point the camera skyward, and a holographic arc shows projected intrusion vectors plus ETA to no-fly boundary.
Voice prompts may complement visuals in high-noise zones. Tested wording such as “Red, Golf-3, two hundred metres, climbing” communicates bearing, grid, and behaviour in under two seconds—critical when guards must keep eyes on the sky, not the phone.
2.6 Offline-first and bandwidth-adaptive behaviour
Utility substations and desert borders rarely enjoy pristine 5G. The app therefore caches vector tiles, ML models, and escalation workflows locally. When the network drops, a lightweight SQLite queue stores signed JSON events; on reconnection, idempotent PUTs replay the backlog without duplicates. Edge-encrypted video thumbnails travel first, followed by full-resolution frames only when bandwidth stabilises, ensuring that command posts see something before see-everything.
2.7 Integration hooks and ecosystem extensibility
Modern security stacks bristle with PSIM dashboards, SIEM alerts, and VMS video walls. A dedicated webhook and GraphQL subscription layer lets integrators mesh drone data with badge-access logs, radar fences, or cyber-threat telemetry. For example, a prison might auto-pan PTZ cameras toward a drone vector while simultaneously locking down cellblock doors. Sensor vendors fare likewise: A-Bots-maintained adapters translate proprietary packets from DJI AeroScope, Dedrone RF-360, or a custom SDR rig into the canonical event schema, ensuring long-term interoperability even as hardware refreshes.
2.8 DevSecOps and regulatory compliance baked in
The full stack ships via GitOps: every manifest, Lambda, and GPU image is version-controlled, security-scanned, and promoted through canary environments in minutes. Secrets ride in Vault-style HSMs; infrastructure as code (Terraform, Crossplane) keeps drift at zero. Encryption is FIPS 140-3 validated, logs meet ISO 27001 retention, and audit evidence packages export directly for FAA or EU Aviation Safety Agency spot checks.
2.9 Performance metrics that matter to the business
Key service-level objectives surface through Prometheus-Grafana dashboards: mean time to detect < 400ms, p99 push delivery < 900ms, and battery impact < 7% per 8-hour shift on a typical Android ruggedised handset. Automated synthetic tests spawn simulated drones overnight, sampling routes and weather profiles that beat real-world variance into the codebase before guards start their morning brief.
2.10 Why A-Bots.com can deliver in ninety days
Because A-Bots.com has spent a decade blending drone telemetry, computer-vision pipelines, and cross-platform Flutter/React Native frameworks, the team boots new projects from a library of hardened micro-services, sensor SDK adapters, and UX widgets. That head start turns a daunting multi-vendor integration into a 90-day MVP with baseline RF, acoustic, and optical fusion, plus a branded mobile shell ready for on-site pilots. Subsequent sprints layer enterprise extras—multi-tenant dashboards, white-label builds for system integrators, and AI model updates—without rewriting core plumbing.
In short, the path from sensors to screen is neither linear nor trivial, yet a disciplined architecture—edge normalisation, resilient message buses, cloud MLOps, zero-trust APIs, and an operator-tested UX—turns chaotic airspace into a stream of actionable insights. The next section will map a concrete implementation roadmap, showing timelines, resource allocation, and cost models that decision-makers can use to green-light a production rollout.
3. Custom Implementation Roadmap with A-Bots.com
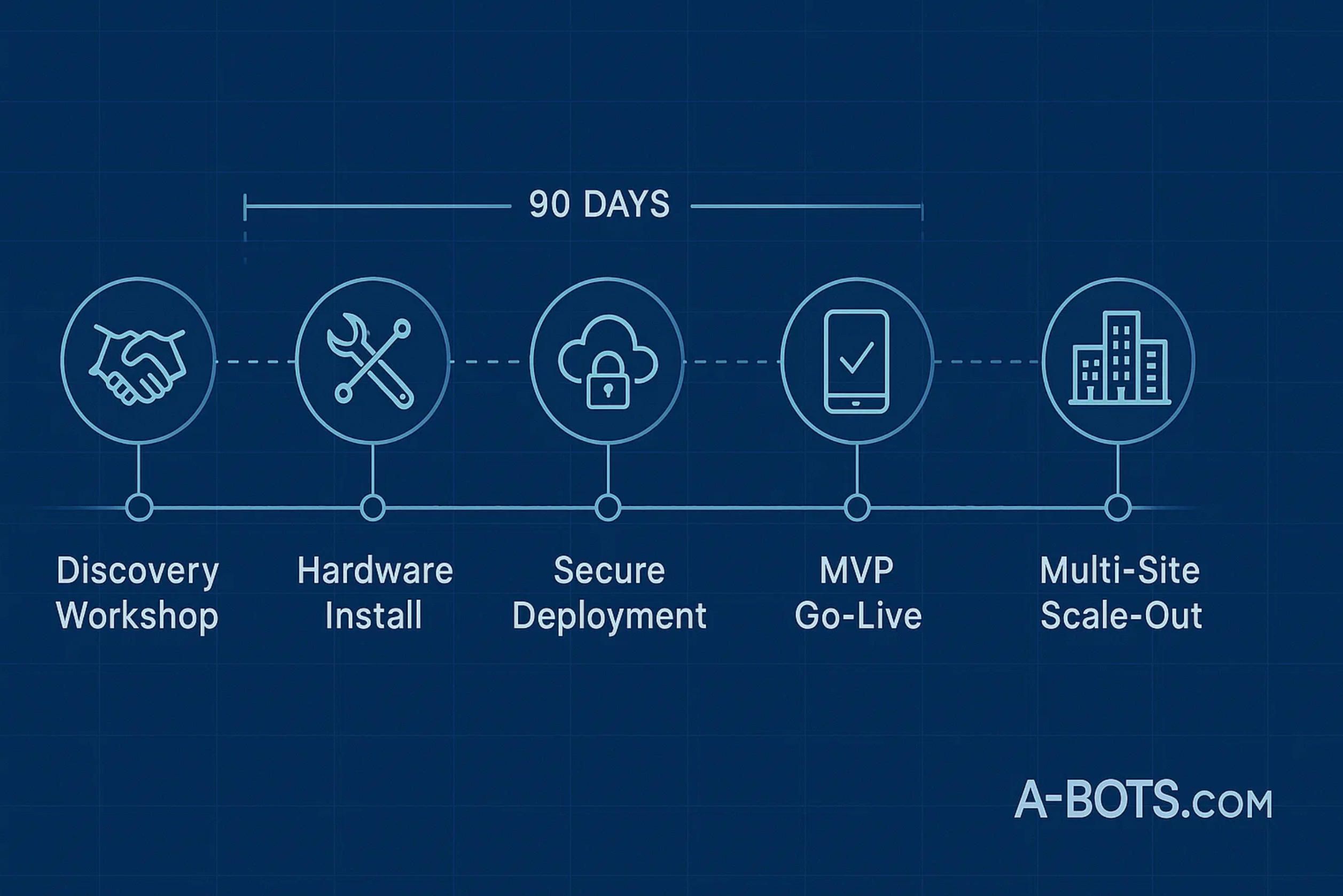
A successful drone-detection initiative begins long before a sensor touches a fence line or a mobile app lands in an operator’s hand. The first milestone is a discovery sprint that A-Bots.com conducts on site with security, IT, and compliance stakeholders. Over three to five days our architects capture the facility’s physical contours, RF spectrum conditions, and incident history, while product strategists interview frontline guards to understand cognitive load and decision-making bottlenecks. That qualitative data is merged with quantitative air-risk modelling produced from public ADS-B feeds and proprietary drone-sighting heat-maps. The output is not a slide deck but a living threat model expressed in MITRE ATT&CK-style kill-chain diagrams and a machine-readable JSON schema that later drives automated testing. By the end of week one the client already owns a structured backlog of user stories tied to measurable service-level objectives such as mean time to detect, false-positive ceilings, and evidence-packaging turnaround.
With scope anchored, the team transitions into a 90-day minimum viable product phase that runs three parallel tracks. Track one configures edge hardware: SDR pods are flashed with a signed firmware that speaks the canonical protobuf dialect, acoustic arrays receive a site-specific transfer-learning pass to exclude local machinery noise, and existing CCTV poles are retro-fitted with EO/IR mini-gimbals. Track two stands up the cloud backbone in the client’s preferred jurisdiction—AWS us-east-1 for a U.S. utility, Azure Germany North for an EU airport, or an on-prem Rancher cluster for defence contractors behind an air gap. Terraform modules written and maintained by A-Bots.com stamp out identical staging and production environments, while GitHub Actions enforce security scans on every container. Track three focuses on operator experience: a React Native shell is branded in the client’s colours, the geospatial SDK is wired to Mapbox or Cesium depending on 2-D versus 3-D needs, and voice prompts are localised into the language mix used on the ground. Weekly stakeholder demos ensure that even early alpha builds align with guard workflows, eliminating surprise feature gaps on day 90.
Once the MVP survives live-fire drills—often a weekend of tethered drone flights scripted to simulate incursions—the roadmap widens toward enterprise scale. Multi-site orchestration is activated through Kubernetes Federation, enabling a single pane of glass for regional security centres while preserving data sovereignty boundaries between countries. Tenancy is abstracted so that headquarters can monitor aggregate metrics but each facility retains command autonomy. At this stage the CI/CD pipeline promotes model updates on a blue-green schedule: new acoustic fingerprints or RF signatures roll out overnight with automatic rollback triggers if confidence scores slip below threshold. Because many customers partner with systems integrators, A-Bots.com offers a white-label build pipeline in which the same codebase outputs custom APKs and iOS bundles under a partner’s brand, complete with separate telemetry buckets and billing endpoints.
Regulatory alignment is stitched into every layer rather than sprinkled at the end. For U.S. critical infrastructure the platform exports STIX-formatted indicators directly into CISA reporting portals; for European airports the data-retention policy complies with the GDPR “storage limitation” principle, purging non-incident video after 30 days while hashing frames to permit later integrity checks. Encryption keys are rotated by HashiCorp Vault and mirrored to hardware security modules that meet FIPS 140-3 Level 3. All service-to-service calls enforce SPIFFE identities, and audit trails are signed with a hardware root of trust so that forensic artefacts stand up in court.
Scalability does not sacrifice cost discipline. Edge containers dynamically downscale video frame rates during network congestion, and Lambda-style GPU pools spin up only when nightly retraining jobs exceed CPU capacity. Prometheus feeds a Grafana board that not only tracks p99 latency but also projects monthly cloud expenditure, giving finance teams early warning if camera upgrades or sensor density threatens the operating budget. On the handset side the mobile SDK lazily loads geofences and model weights, keeping battery drain under seven percent during an eight-hour shift on common ruggedised Android devices.
Change management is streamlined through a customer success cadence rather than ad-hoc tickets. A-Bots.com deploys a dedicated Slack Connect channel where automated bots post every new feature flag toggled in staging; security officers can A/B test improvements without waiting for quarterly releases. Quarterly on-site workshops revisit the original threat model, overlaying the last ninety days of detection telemetry to validate assumptions or surface new blind spots. When the data reveals that most incursions approach from the southwest perimeter, for example, the roadmap pivots toward denser sensor coverage there, and the mobile UX highlights that corridor with a higher-contrast palette.
Finally, engagement models remain flexible because no two organisations share the same procurement DNA. Clients may opt for a classic fixed-price milestone contract covering discovery through MVP, then switch to a time-and-materials retainer for incremental enhancements. Others bundle the platform into an operational-expenditure subscription, transferring hardware ownership and lifecycle management to A-Bots.com entirely. In every scenario the intellectual property developed—be it a new acoustic classifier or a data-fusion heuristic fine-tuned for urban canyons—re-enters a shared knowledge base that benefits the entire customer community through versioned SDK updates.
The resulting roadmap is thus neither a rigid Gantt chart nor a vague “agile journey” cliché. It is a concrete, security-first, DevSecOps-driven sequence of deliverables that moves from threat modelling to live deployment in three months and then iterates perpetually. By embedding compliance, cost control, and operator feedback loops from day zero, A-Bots.com turns a complex, multi-vendor counter-UAS challenge into a sustainable, upgradeable, and auditable mobile solution that keeps evolving as drone technology and airspace regulations do.

✅ Hashtags
#DroneDetection
#CounterUAS
#AirspaceSecurity
#MobileAppDev
#ABots
#IoTSecurity
#UAVSafety
#EdgeAI
Other articles
Explore DoorDash and Wing’s drone delivery DoorDash and Wing are quietly rewriting last-mile economics with 400 000+ aerial drops and 99 % on-time metrics. This deep dive maps milestones, performance data, risk controls and expansion strategy—then explains how A-Bots.com turns those insights into a fully-featured drone-delivery app for your brand.
PropelSW App (2025 Guide) — Download, Restore and Fly The original Propel Star Wars Battle Drones app disappeared from official stores, but pilots still crave its flight trainer. Our in-depth 2,800-word guide explains exactly how to locate a clean PropelSW APK or TestFlight build, sideload it safely, pair your vintage controller and update firmware without bricking your X-Wing. We also review Liftoff Micro Drones, FPV Freerider and DRL Simulator as risk-free practice arenas, then outline how A-Bots.com can deliver a cloud-ready, licence-friendly successor with AR overlays and sub-40 ms video latency.
Litchi vs DJI Fly Choosing between Litchi and DJI Fly now shapes mission safety, data ownership and long-term budgets. This in-depth 2025 guide dissects both ecosystems: advanced waypoint scripting, Remote ID readiness, device and firmware compatibility, hidden operating costs and real-world use cases from cinematic shoots to corridor inspections. Drawing on community reports and the latest SDK 5 roadmap, it helps pilots, surveyors and enterprise managers decide which app delivers the most value—and explains why A-Bots.com’s custom-built drone software can merge the strengths of each platform into a single, brand-tuned solution.
Drone Survey Software: Pix4D vs DroneDeploy The battle for survey-grade skies is heating up. In 2025, Pix4D refines its lab-level photogrammetry while DroneDeploy streamlines capture-to-dashboard workflows, yet neither fully covers every edge case. Our in-depth article dissects their engines, accuracy pipelines, mission-planning UX, analytics and licensing models—then reveals the “SurveyOps DNA” stack from A-Bots.com. Imagine a modular toolkit that unites terrain-aware flight plans, on-device photogrammetry, AI-driven volume metrics and airtight ISO-27001 governance, all deployable on Jetson or Apple silicon. Add our “60-Minute Field-to-Finish” Challenge and white-label SLAs, and you have a path to survey deliverables that are faster, more secure and more precise than any off-the-shelf combo. Whether you fly RTK-equipped multirotors on construction sites or BVLOS corridors in remote mining, this guide shows why custom software is now the decisive competitive edge.
Top stories
Copyright © Alpha Systems LTD All rights reserved.
Made with ❤️ by A-BOTS
